I. Introduction
A. Definition of Blockchain Technology:
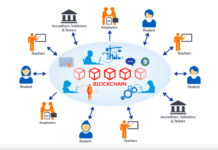
Blockchain technology is a decentralized and distributed digital ledger system that records transactions across a network of computers, ensuring transparency, security, and immutability of data. It operates on the principle of consensus among network participants, who validate and add new transactions to the blockchain.
Here are some key elements of blockchain technology:
- Decentralization: In a traditional centralized system, a single entity (like a bank or government) controls the database. In contrast, a blockchain operates on a network of nodes (computers) that collectively maintain the ledger. This decentralization reduces the risk of a single point of failure and makes it more resilient to attacks.
- Distributed Ledger: Blockchain data is stored in a chain of blocks, with each block containing a batch of transactions. These blocks are linked together in chronological order, creating a continuous and tamper-evident record of all transactions.
- Cryptography: Blockchain relies on cryptographic techniques to secure data and control access. Each participant has a private key to sign transactions and a public key to verify them. This ensures the integrity and authenticity of transactions.
- Consensus Mechanisms: To add a new block to the chain, network participants must agree on the validity of transactions. Different blockchains use various consensus mechanisms, such as Proof of Work (PoW) and Proof of Stake (PoS), to achieve this agreement.
Examples:
- Bitcoin: The first and most well-known blockchain, Bitcoin uses PoW to secure its network. Miners compete to solve complex mathematical puzzles to validate transactions and earn rewards.
- Ethereum: Another popular blockchain, Ethereum, initially used PoW but has transitioned to PoS. It’s known for its smart contract functionality, allowing developers to build decentralized applications (DApps).
- Hyperledger Fabric: An enterprise-grade blockchain platform, Hyperledger Fabric uses a permissioned network, where only authorized participants can validate transactions. It’s designed for businesses and consortiums.
B. Significance of Blockchain Security:
Blockchain security is of paramount importance due to several critical reasons:
- Immutability: Once data is added to the blockchain, it becomes nearly impossible to alter or delete. This property ensures the integrity of historical records and prevents fraudulent activities. For example, in the case of Bitcoin, once a transaction is confirmed and added to the blockchain, it cannot be reversed.
- Transparency: Blockchain provides a transparent and publicly accessible ledger. Anyone can verify transactions, which fosters trust among users. For instance, in supply chain management, participants can track the origin and journey of products using blockchain, ensuring authenticity and quality.
- Data Integrity: Cryptographic hashing and consensus mechanisms make it extremely difficult for malicious actors to tamper with data. For example, in healthcare, patient records stored on a blockchain can be securely shared among authorized healthcare providers without fear of unauthorized alterations.
- Resilience: Decentralization and redundancy across nodes make blockchain networks resistant to single points of failure. This resilience is crucial in scenarios where uptime and data availability are critical, such as in financial systems.
- Security Tokens and Assets: Blockchain enables the creation of security tokens representing ownership of real-world assets like real estate or company shares. Robust security measures ensure that these tokens are protected from theft or fraud.
- Smart Contracts: Smart contracts are self-executing agreements with predefined rules. They are executed automatically when conditions are met. Blockchain security ensures that these contracts are tamper-proof and trustworthy, making them useful in various applications, including legal agreements and financial services.
Blockchain security is vital because it underpins the trust and reliability of decentralized systems, allowing them to operate securely in various industries, from finance to healthcare and supply chain management. Its immutability, transparency, and resilience make it a transformative technology for securing data and transactions in the digital age.
II. Understanding Blockchain Technology
Let’s delve into a detailed explanation of blockchain technology with a focus on its architecture, key components, and the process of recording and validating transactions.
A. Key Components of a Blockchain:
- Transactions: Transactions are the fundamental data units on a blockchain. They record the exchange of assets or information between participants. For example, in a cryptocurrency blockchain like Bitcoin, a transaction represents the transfer of digital coins from one user’s wallet to another.
- Blocks: Transactions are grouped together into blocks. A block typically contains a set of validated transactions, a reference to the previous block (forming a chain), and a unique identifier called a block hash.
- Blockchain Network: The network consists of nodes (computers) that participate in the blockchain. Some nodes may be miners (in PoW systems) or validators (in PoS systems) responsible for adding new blocks.
- Consensus Rules: Each blockchain has its own consensus rules that determine how participants agree on the validity of transactions and the process of adding new blocks. For example, in PoW-based blockchains like Bitcoin, miners compete to solve complex mathematical puzzles to validate transactions.
- Smart Contracts (Optional): Smart contracts are self-executing, programmable agreements that automatically execute predefined actions when certain conditions are met. They are a key component in platforms like Ethereum, enabling decentralized applications and automated processes.
B. How Transactions Are Recorded and Validated:
- Transaction Submission: Users initiate transactions by creating and signing them with their private keys. These transactions are then broadcasted to the blockchain network.
- Transaction Verification: Transactions are received by nodes in the network. Each node verifies the transaction’s validity, checking factors like digital signatures, available funds, and adherence to network rules.
- Transaction Pool: Valid transactions are added to a pool of pending transactions waiting to be included in the next block. Miners or validators select transactions from this pool based on criteria such as transaction fees (incentives).
- Consensus Mechanism: In PoW, miners compete to solve a cryptographic puzzle. The first miner to solve it broadcasts the solution, and if other nodes agree, the new block is added to the chain. In PoS, validators are chosen to create new blocks based on their stake in the network.
- Block Addition: Once a block is added to the blockchain, it is distributed to all nodes, and the transactions within it are considered confirmed. The process then repeats with new transactions being added to the pool.
III. Security Threats in Blockchain
A. Overview of Common Blockchain Security Threats:
Blockchain technology is generally considered secure, but it’s not immune to various security threats. Here are some common blockchain security threats:
- Double-Spending Attacks:
- Description: In a double-spending attack, a malicious actor attempts to spend the same cryptocurrency or digital asset more than once by creating multiple copies of a transaction. This undermines the trust and value of the blockchain.
- Example: The Bitcoin network is designed to prevent double spending through the Proof of Work (PoW) consensus mechanism. While it has not experienced a successful double-spending attack, smaller cryptocurrencies with lower hash rates have been vulnerable to such attacks.
- 51% Attacks:
- Description: A 51% attack occurs when an entity or group controls more than 50% of the computational power (hash rate) of a blockchain network. With majority control, they can manipulate transactions, double-spend, and disrupt the network’s normal functioning.
- Example: In 2018, the cryptocurrency Verge suffered multiple 51% attacks. Attackers gained majority control of the network, causing significant disruptions.
- Sybil Attacks:
- Description: In a Sybil attack, an attacker creates a large number of fake nodes or identities on the network to gain influence or control. This undermines trust and decentralization by skewing decision-making processes.
- Example: While not commonly reported on public blockchains like Bitcoin and Ethereum, Sybil attacks have been observed on smaller or less-secure networks, especially those with low barriers to entry.
- Smart Contract Vulnerabilities:
- Description: Smart contracts are susceptible to various vulnerabilities, including coding errors, logic flaws, and exploits that can lead to unintended consequences. These vulnerabilities can result in the loss of funds or disruption of decentralized applications (DApps).
- Example: The DAO (Decentralized Autonomous Organization) hack in 2016 exploited a vulnerability in a smart contract on the Ethereum blockchain. Hackers drained approximately $50 million worth of Ether from the DAO, leading to a contentious hard fork to reverse the effects of the attack.
B. Real-World Examples of Security Breaches:
- Mt. Gox Exchange:
- Description: Mt. Gox was once one of the largest Bitcoin exchanges in the world. It suffered multiple security breaches and ultimately filed for bankruptcy in 2014. Approximately 850,000 Bitcoins belonging to users were lost or stolen.
- Impact: This incident highlighted the vulnerability of centralized exchanges and the importance of securing user funds.
- Parity Wallet Multi-Signature Bug:
- Description: In 2017, a vulnerability in a multi-signature smart contract wallet on the Ethereum network was exploited, leading to the freezing of over $150 million worth of Ether.
- Impact: The incident highlighted the need for rigorous security audits of smart contracts and the potential risks associated with complex blockchain applications.
- Binance Security Breach:
- Description: In 2019, Binance, one of the world’s largest cryptocurrency exchanges, experienced a security breach where hackers stole over 7,000 Bitcoins (approximately $40 million at the time).
- Impact: Binance responded swiftly by covering the losses with its SAFU (Secure Asset Fund for Users) and enhancing its security measures.
- FTX Exchange Collapse:
- Description: The fortunes of FTX and its founder and former CEO, Bankman-Fried, are linked. In November 2022, cryptocurrency exchange FTX collapsed over a period of 10 days. Following a report suggesting potential leverage and solvency concerns, the exchange faced a liquidity crisis and tried to negotiate a bailout by rival Binance that quickly fell through. Its CEO was later arrested, extradited to the U.S., released on a $250 million bond, and now faces trial.
- Impact: The future of FTX as a cryptocurrency exchange is in serious jeopardy. As of mid-November 2022, withdrawals were disabled and a notice on the FTX website says the company “strongly advise[s] against depositing.” The implications for the future of FTX, and the collapse’s impact on the broader cryptocurrency industry, are ongoing and difficult to assess.
These real-world examples illustrate that while blockchain technology offers robust security features, it is not immune to threats and vulnerabilities.
Security breaches can have significant financial and reputational consequences, underscoring the importance of ongoing security practices and measures in the blockchain ecosystem.
IV. Key Principles of Blockchain Security
A. Decentralization and Its Role in Security:
Decentralization is a fundamental principle of blockchain security, and it plays a crucial role in several ways:
- Resilience: A decentralized network has no single point of failure. Even if some nodes go offline or are compromised, the network can continue to operate. This resilience is essential for ensuring the availability and security of the blockchain.
- Trust lessness: Decentralization reduces the need for trust in a central authority. Users can transact directly with one another without relying on intermediaries, which can be susceptible to corruption or security breaches.
- Security against Attacks: Decentralization makes it more challenging for malicious actors to manipulate or control the network. For example, in a 51% attack, controlling the majority of a decentralized network’s computational power becomes much more difficult.
Example: Bitcoin, the pioneering cryptocurrency, operates on a highly decentralized network of nodes worldwide. This decentralization has contributed to its robustness and resistance to attacks since no single entity can control the majority of the network’s computational power.
B. Consensus Algorithms and Their Impact on Security:
Consensus algorithms are protocols that ensure all network participants agree on the state of the blockchain. They have a direct impact on security:
- Proof of Work (PoW): PoW requires miners to solve complex mathematical puzzles to validate transactions and add new blocks. This mechanism makes it computationally expensive and time-consuming to manipulate the blockchain.
- Proof of Stake (PoS): PoS relies on validators who hold and “stake” cryptocurrency as collateral to confirm transactions. It’s generally more energy-efficient than PoW and can be more resistant to certain attacks.
- Delegated Proof of Stake (DPoS), Practical Byzantine Fault Tolerance (PBFT), etc.: Other consensus algorithms have their own security characteristics and trade-offs.
Example: Ethereum, the second-largest blockchain by market capitalization, is transitioning from PoW to PoS to improve energy efficiency and security. PoS is expected to make the network more secure by requiring validators to lock up significant amounts of cryptocurrency as collateral.
C. Transparency and Auditability:
Transparency and auditability are key principles of blockchain security:
- Transparency: Every transaction and block on a blockchain is publicly visible to all participants. This transparency reduces the risk of fraudulent activity and promotes trust.
- Auditability: Blockchain’s immutable ledger allows anyone to verify the history of transactions. This auditability is particularly important in sectors like supply chain management and finance, where trust and traceability are critical.
Example: In supply chain management, companies like IBM and Walmart are using blockchain technology to create transparent and auditable records of the origin and journey of products. This ensures the authenticity of products and helps prevent counterfeiting.
D. Cryptographic Techniques for Securing Data:
Blockchain relies heavily on cryptography to secure data and transactions:
- Hashing: Cryptographic hash functions are used to create unique, fixed-length representations of data. These hashes ensure the integrity of data on the blockchain.
- Digital Signatures: Participants use private keys to create digital signatures for transactions. Public keys are used to verify the authenticity of these signatures, ensuring that transactions are valid and secure.
Example: Bitcoin uses cryptographic hashing to secure transactions. Each block contains a hash of the previous block, creating a tamper-evident chain. Digital signatures are used to prove ownership of Bitcoin addresses and validate transactions.
E. Role of Permissioned vs. Permissionless Blockchains:
Permissioned and permissionless blockchains have different security implications:
- Permissionless Blockchains: These are open to anyone, allowing for decentralized and trustless transactions. They are often more secure against censorship but may have higher energy consumption.
- Permissioned Blockchains: These restrict access to trusted participants. They provide more control and privacy but may sacrifice some decentralization and trustlessness.
Example: Ethereum and Bitcoin are examples of permissionless blockchains, where anyone can participate. In contrast, Hyperledger Fabric is a permissioned blockchain often used in enterprise settings where access control is crucial for security and compliance.
These key principles of blockchain security, including decentralization, consensus algorithms, transparency, cryptography, and the choice between permissioned and permissionless blockchains, collectively contribute to the overall security and trustworthiness of blockchain networks and applications.
V. Best practices of blockchain security
Here are the best practices for blockchain security, along with examples:
A. Secure Wallet Management:
Hot Wallets vs. Cold Wallets:
Hot Wallets: These are wallets connected to the internet and are used for day-to-day transactions. They are more susceptible to online attacks. It’s essential to use strong encryption, multi-factor authentication (MFA), and keep only a limited amount of cryptocurrency in hot wallets.
Cold Wallets: These are wallets not connected to the internet, making them less vulnerable to online attacks. They are typically used for long-term storage of cryptocurrencies. Hardware wallets (e.g., Ledger Nano S) and paper wallets are common types of cold wallets.
Example: Cryptocurrency exchanges often use a combination of hot wallets for liquidity and cold wallets for storing most user funds securely. For instance, Coinbase holds the majority of user funds in cold storage.
Multi-Signature Wallets:
Multi-signature (multisig) wallets require multiple private keys to authorize a transaction. For example, a 2-of-3 multisig wallet may require two out of three private key holders to approve a transaction. This adds an extra layer of security by reducing the risk of a single point of failure.
Example: Ethereum-based multisig wallets have been widely adopted for secure storage of Ether and tokens. Gnosis Safe is a popular multisig wallet that allows users to define custom signing requirements.
B. Smart Contract Development and Auditing:
- Code Review and Auditing: Before deploying a smart contract on the blockchain, thoroughly review and audit the code. Smart contracts are immutable once deployed, and any vulnerabilities or bugs can result in irreversible losses. Third-party auditing firms can help identify potential issues.
- Example: The infamous DAO (Decentralized Autonomous Organization) hack on the Ethereum blockchain in 2016 was the result of a smart contract vulnerability. The incident led to a contentious hard fork to recover lost funds.
- Testing: Conduct comprehensive testing, including unit tests, integration tests, and security tests, to ensure the smart contract behaves as intended. Test on testnet environments before deploying to the mainnet.
C. Regular Software Updates and Patch Management:
- Node and Wallet Software: Keep blockchain nodes and wallet software up to date with the latest security patches and updates. Vulnerabilities discovered in older versions can be exploited by attackers.
- Example: Bitcoin Core regularly releases updates with bug fixes and security enhancements. Users are encouraged to upgrade to the latest version to stay secure.
D. Identity and Access Management:
- Authentication: Use strong authentication mechanisms, such as multi-factor authentication (MFA), to secure access to wallets, nodes, and blockchain-related services. Avoid sharing private keys or sensitive information.
- Example: Many cryptocurrency exchanges and wallet providers offer MFA options to enhance the security of user accounts.
- Access Control: Implement strict access control policies, limiting access to sensitive systems and data only to authorized personnel. Ensure that employees and administrators have the least privilege necessary to perform their duties.
E. Secure Key Management:
- Key Generation and Storage: Generate cryptographic keys using secure, reputable methods, and store them in hardware security modules (HSMs) or secure offline storage. Protect private keys from unauthorized access or theft.
- Example: Ledger Nano S and Trezor are popular hardware wallets that securely store private keys offline.
- Key Backups: Create secure backups of private keys and store them in physically secure locations. Ensure that recovery procedures are well-documented and tested.
These best practices for blockchain security are essential for protecting assets, data, and smart contracts in the blockchain ecosystem. Security should be a top priority for individuals, organizations, and blockchain developers to mitigate risks and prevent potential attacks or losses.
VI. Regulatory and compliance considerations
Let us explore the regulatory and compliance considerations in the context of blockchain security, along with relevant examples:
A. Overview of Global Regulations Related to Blockchain:
Blockchain technology and cryptocurrencies have prompted various governments and regulatory bodies worldwide to develop regulations to address potential risks and ensure compliance.
Regulations can vary significantly from one country to another. Here are some notable global regulatory trends:
- Securities and Exchange Commission (SEC) in the United States: The SEC has been actively involved in regulating cryptocurrencies and Initial Coin Offerings (ICOs). It has provided guidelines on how cryptocurrencies and tokens should be classified, often considering them as securities.
- Financial Action Task Force (FATF): An intergovernmental organization, FATF has introduced recommendations for combating money laundering and terrorist financing in the cryptocurrency space. These recommendations encourage countries to implement stricter Know Your Customer (KYC) and Anti-Money Laundering (AML) measures.
- European Union (EU) Regulations: The EU has introduced the Fifth Anti-Money Laundering Directive (5AMLD), which includes provisions for regulating cryptocurrency exchanges and wallet providers, imposing KYC and AML requirements.
- China’s Ban on Cryptocurrency Activities: China has taken a strict stance on cryptocurrencies, banning ICOs and cryptocurrency trading platforms. However, it has shown interest in blockchain technology for various applications.
B. Compliance Requirements for Blockchain Projects:
Compliance requirements for blockchain projects typically revolve around KYC, AML, and securities regulations. Here are some key considerations:
- KYC and AML: Most jurisdictions require blockchain projects, especially those involved in cryptocurrency trading or token sales, to implement robust KYC and AML procedures. This involves verifying the identity of users and monitoring transactions for suspicious activities.
- Example: Coinbase, a major cryptocurrency exchange, enforces KYC and AML procedures to ensure compliance with U.S. regulations.
- Securities Regulation: If a blockchain project issues tokens or cryptocurrencies that are deemed securities, it may need to comply with securities regulations. This can involve registration with regulatory authorities and providing disclosure documents to investors.
- Example: In the United States, the SEC has taken enforcement actions against ICOs that were found to have violated securities laws, such as the case of “Munchee Inc.” SEC brought a non-fraud-related ICO enforcement action, halting an ongoing ICO by Munchee Inc. that was neither registered nor exempt from registration and causing Munchee Inc. to refund proceeds before any tokens were delivered to investors.
- Taxation: Blockchain transactions may have tax implications, and projects need to comply with tax laws in their respective jurisdictions. This includes reporting and paying taxes on cryptocurrency gains.
- Example: The Internal Revenue Service (IRS) in the United States provides guidance on cryptocurrency taxation.
C. The Role of Privacy and Data Protection in Blockchain:
Blockchain technology is known for its transparency, but it also raises privacy and data protection concerns:
- Public vs. Private Blockchains: Public blockchains, like Bitcoin and Ethereum, are highly transparent, with all transactions visible to anyone. In contrast, private blockchains can offer more privacy by restricting access to authorized participants.
- Privacy Coins: Some cryptocurrencies, known as privacy coins (e.g., Monero, Zcash), are designed to provide enhanced privacy features, such as anonymous transactions.
- Example: Monero transactions use advanced cryptographic techniques to obfuscate transaction details, making it difficult to trace transactions and user identities.
- GDPR and Data Protection: The European General Data Protection Regulation (GDPR) applies to blockchain projects that handle personal data. Projects must ensure that they comply with GDPR requirements when dealing with user data.
- Example: Blockchain projects that involve user data, such as identity verification or healthcare records, must implement GDPR-compliant data protection measures.
Thus, blockchain technology operates within a complex regulatory landscape that varies by jurisdiction. Compliance with regulations related to KYC, AML, securities, and data protection is crucial for blockchain projects to operate legally and securely.
Privacy considerations, especially in the context of public vs. private blockchains and privacy coins, also play a significant role in blockchain security and compliance.
VII. Security Challenges in Public vs. Private Blockchains
A. Comparison of Security Considerations:
Public Blockchains:
- Decentralization: Public blockchains are typically more decentralized, which can enhance security by reducing the risk of a single point of failure. However, this can also introduce challenges related to consensus and governance.
- Permissionless: Anyone can participate in public blockchains, which can lead to increased risks of spam, Sybil attacks, and malicious activity. The open nature of public blockchains can be both a strength and a weakness.
- Transparency: Public blockchains offer high transparency, making all transactions and data publicly accessible. While this transparency can enhance trust, it can also raise privacy concerns.
Private Blockchains:
- Centralized Control: Private blockchains are often more centralized, with a limited number of trusted participants. This centralization can simplify governance and consensus but can also introduce single points of failure.
- Permissioned: Access to private blockchains is restricted to authorized participants, reducing the risk of malicious actors. However, this can lead to concerns about transparency and trust among participants.
- Privacy: Private blockchains can offer enhanced privacy features by limiting access to data. However, this can also raise concerns about transparency and auditability.
B. Use Cases for Public and Private Blockchains:
Public Blockchains:
- Cryptocurrencies: Public blockchains like Bitcoin and Ethereum are widely used for peer-to-peer transactions and as stores of value.
- Global Supply Chain: Public blockchains can track the provenance and movement of goods, ensuring transparency and authenticity.
- Decentralized Finance (DeFi): Public blockchains enable decentralized lending, borrowing, and trading of assets without intermediaries.
- Public Records: Land registries and identity verification can benefit from the transparency and immutability of public blockchains.
Private Blockchains:
- Enterprise Solutions: Private blockchains are often used by businesses for supply chain management, record-keeping, and intra-organizational transactions.
- Consortiums: Multiple organizations in an industry can collaborate on a private blockchain to streamline processes and share data securely.
- Government Applications: Governments may use private blockchains for secure record-keeping, voting systems, or managing citizen data.
- Healthcare: Private blockchains can store and share sensitive patient data securely among healthcare providers.
C. Mitigating Security Risks in Each Context:
Public Blockchains:
- Consensus Mechanisms: Public blockchains rely on robust consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to maintain security. Participation from a large number of nodes helps prevent centralization.
- User Education: Users must be educated on best practices for wallet security, including the use of hardware wallets, secure passwords, and avoidance of phishing scams.
- Privacy Solutions: Projects like Zcash and Monero offer enhanced privacy features on public blockchains, addressing privacy concerns.
Private Blockchains:
- Access Control: Strict access control and identity management are crucial to ensure that only authorized participants can join the network. This mitigates internal security risks.
- Governance: Establishing clear governance mechanisms among participants is essential to address centralization concerns and maintain trust.
- Data Encryption: Implementing strong encryption and data access controls can protect sensitive information on private blockchains.
- Auditability: While private blockchains provide more privacy, they should still offer mechanisms for auditability and transparency among authorized parties.
Example: Hyperledger Fabric is an example of a private blockchain framework that allows for fine-grained access control, ensuring that only authorized participants can access the network and its data.
Public blockchains emphasize decentralization and transparency, while private blockchains prioritize centralization and control.
Mitigating security risks in each context involves addressing the unique challenges while adhering to best practices and industry standards. The choice between public and private blockchains depends on the specific use case and the desired balance between security, transparency, and control.
VIII. Case Studies in Blockchain Security
A. Real-World Examples of Successful Security Implementations:
- Ethereum 2.0 Transition (2020):
- Security Implementation: Ethereum, one of the largest blockchain platforms, initiated its transition from a Proof of Work (PoW) consensus mechanism to a more energy-efficient Proof of Stake (PoS) system with Ethereum 2.0. This transition aimed to enhance the security and sustainability of the network.
- Outcome: The transition has been successful so far, with a growing number of validators securing the network, reducing the energy consumption associated with PoW. This implementation demonstrates the commitment to improving security and sustainability in blockchain ecosystems.
- IBM Food Trust (2017):
- Security Implementation: IBM Food Trust is a blockchain-based platform that provides transparency and traceability in the food supply chain. It allows participants to track the origin and journey of food products, reducing the risk of contamination and fraud.
- Outcome: IBM Food Trust has successfully improved food safety and transparency. It has been adopted by major food companies like Walmart and Nestlé to enhance the security and quality of their supply chains.
Here are some examples of successful blockchain security implementations in the last two years:
- Xage Security: A California-based cybersecurity firm that leverages blockchain to protect industrial IoT networks.
- Everledger Diamond Platform: A real-world blockchain use case for the diamond supply chain developed by Everledger using the Hyperledger platform. Through this platform, Everledger traces the provenance of a diamond, and thus helps prevent illicit trading and fraud.
- BitPesa: A digital foreign exchange and payments platform working in the Sub-Saharan Africa to offer easier business transactions by increasing the speed of payments and reducing third party fees associated with them.
- Walmart: Successfully ran a test pilot for a Blockchain in supply chain that reduced the time to track sliced mangoes to just about 2.2 seconds. With its Blockchain endeavor, Walmart is planning to improve transparency, reduce wastage, and effectively manage contamination.
B. Lessons Learned from High-Profile Security Breaches:
- The DAO Hack (2016):
- Security Breach: The Decentralized Autonomous Organization (DAO) on the Ethereum blockchain suffered a significant security breach due to a vulnerability in its smart contract code. Hackers drained approximately $50 million worth of Ether.
- Lessons Learned: This incident highlighted the importance of code audits, rigorous testing, and secure coding practices for smart contracts. It also led to a contentious hard fork to reverse the effects of the hack.
- Mt. Gox Exchange (2014):
- Security Breach: Mt. Gox, once a major Bitcoin exchange, filed for bankruptcy after losing approximately 850,000 Bitcoins belonging to users due to security breaches and poor internal controls.
- Lessons Learned: The Mt. Gox incident emphasized the need for robust security measures, including cold storage of funds, regular security audits, and transparency in exchange operations. It also served as a reminder of the importance of regulatory compliance in the cryptocurrency space.
C. How Organizations Recovered from Security Incidents:
- The DAO Hard Fork and Ethereum (2016):
- Recovery: To recover the stolen funds from The DAO hack, the Ethereum community decided to perform a hard fork, resulting in two separate blockchains: Ethereum (ETH) and Ethereum Classic (ETC). Ethereum continued to evolve and improve its security features.
- Outcome: Ethereum has grown to become one of the leading blockchain platforms, implementing security enhancements and learning from the DAO incident.
- Binance Security Breach (2019): Recovery: After a security breach that resulted in the theft of over 7,000 Bitcoins, Binance, one of the world’s largest cryptocurrency exchanges, quickly responded by covering the losses with its SAFU (Secure Asset Fund for Users). It also enhanced its security measures and introduced security-related initiatives.
- Outcome: Binance continued to operate successfully, with a focus on improving security. The incident demonstrated the importance of having contingency plans in place to protect user funds.
Real-world case studies in blockchain security illustrate both successful implementations and the lessons learned from high-profile security breaches.
These incidents highlight the critical role of security measures, code audits, transparency, and the ability to respond swiftly to security incidents in the blockchain industry.
Recovering from security breaches often requires a combination of technical solutions and community consensus, which can help strengthen the overall security of blockchain ecosystems.
IX. Future Trends in Blockchain Security
The future of blockchain security will likely involve the adoption of emerging technologies like zero-knowledge proofs and homomorphic encryption, as well as leveraging AI and machine learning for threat detection and prevention.
Additionally, regulatory changes are expected to play a significant role in shaping the security landscape for blockchain networks, influencing compliance requirements and best practices for both individuals and organizations in the blockchain space.
The future trends in blockchain security are as follows:
A. Emerging Security Technologies:
- Zero-Knowledge Proofs (ZKPs): Zero-knowledge proofs, like zk-SNARKs and zk-STARKs, are cryptographic techniques that allow one party to prove to another party that a statement is true without revealing any information about the statement itself. ZKPs enhance privacy and confidentiality in blockchain transactions.
- Homomorphic Encryption: This technology allows computation on encrypted data without decrypting it, preserving data privacy. It can be applied to secure data processing within blockchain networks, especially in scenarios involving sensitive data.
- Quantum-Resistant Cryptography: With the potential advent of quantum computers, which could break many traditional cryptographic methods, quantum-resistant cryptography is emerging as a future trend. It aims to secure blockchain networks against quantum threats.
- Hardware Security Modules (HSMs): HSMs are physical devices that provide secure key management and cryptographic operations. They are increasingly being used to protect private keys in blockchain networks, especially in enterprise and financial applications.
B. The Role of AI and Machine Learning in Blockchain Security:
- Anomaly Detection: AI and machine learning can analyze large volumes of blockchain data to detect unusual patterns or anomalies that may indicate security breaches or fraudulent activities.
- Predictive Analysis: Machine learning models can predict potential security threats by analyzing historical data and identifying trends and vulnerabilities. This proactive approach allows organizations to address security issues before they occur.
- Behavioral Analysis: AI can be used to analyze the behavior of network participants, helping to identify malicious actors or unusual behavior that may indicate a security threat.
- Privacy-Preserving Techniques: AI can assist in developing privacy-preserving technologies, such as differential privacy and federated learning, to enhance data privacy in blockchain networks.
C. Potential Regulatory Changes Impacting Security:
- Enhanced AML and KYC Regulations: Regulatory authorities may introduce stricter Anti-Money Laundering (AML) and Know Your Customer (KYC) requirements for blockchain-based financial services, exchanges, and wallet providers to combat illicit activities.
- Data Privacy Regulations: As blockchain technology is used for more data-intensive applications, there may be increased scrutiny and regulation related to data protection and privacy, potentially impacting how user data is handled on blockchains.
- Token Regulations: Regulatory frameworks governing cryptocurrencies and tokens may evolve to provide clearer guidelines on their classification, taxation, and security requirements, impacting token issuers and exchanges.
- Cybersecurity Regulations: Governments and regulatory bodies may introduce cybersecurity regulations specific to blockchain networks, mandating security standards and incident reporting procedures.
- International Collaboration: Given the global nature of blockchain, international collaboration on regulatory standards and security practices may become more common to address cross-border security challenges.
X. Ongoing vigilance in blockchain security
Ongoing vigilance is crucial due to the dynamic nature of the blockchain space, the evolving threat landscape, and the need to adapt to technological advancements and regulatory changes.
Encouraging organizations to prioritize blockchain security is essential to safeguard assets, protect reputations, ensure compliance, and gain a competitive advantage in an increasingly blockchain-driven world.
Let’s elaborate on the importance of ongoing vigilance in blockchain security and why organizations should prioritize it:
A. The Importance of Ongoing Vigilance in Blockchain Security:
- Evolving Threat Landscape: The threat landscape in the blockchain space is continuously evolving. New attack vectors and vulnerabilities are discovered, and malicious actors are constantly seeking ways to exploit weaknesses. Ongoing vigilance is essential to adapt to these changing threats.
- Smart Contract Risks: Smart contracts, which automate actions on the blockchain, are susceptible to coding errors and vulnerabilities. Even well-audited contracts can become vulnerable as the blockchain environment changes. Regular code reviews and audits are necessary to identify and mitigate risks.
- Regulatory Changes: Regulatory environments for blockchain and cryptocurrencies are dynamic. New regulations and compliance requirements may be introduced, requiring organizations to adjust their security practices to remain compliant.
- Technology Advancements: As blockchain technology evolves, new features, consensus mechanisms, and cryptographic techniques are developed. Staying updated with technological advancements is vital to implement the latest security measures effectively.
- User Awareness: Users of blockchain systems, whether individuals or organizations, can also be a source of security risks. Phishing attacks, wallet mismanagement, and other human errors can lead to security breaches. Ongoing education and awareness campaigns can help users make informed security decisions.
B. Encouragement for Organizations to Prioritize Blockchain Security:
- Asset Protection: Blockchain networks often involve valuable assets, whether they are cryptocurrencies, digital assets, or sensitive data. Prioritizing security safeguards these assets from theft, fraud, and unauthorized access.
- Brand Reputation: Security breaches can have a severe impact on an organization’s reputation. High-profile incidents can erode trust among users and partners, leading to long-term damage to the brand.
- Legal and Regulatory Compliance: Many jurisdictions impose legal and regulatory obligations on organizations using blockchain technology, particularly in finance and data management. Prioritizing security ensures compliance with these requirements.
- Cost Savings: Preventing security incidents is typically more cost-effective than dealing with the consequences of a breach. Security investments can reduce the risk of financial losses and legal liabilities.
- Competitive Advantage: Organizations that prioritize blockchain security can gain a competitive edge by demonstrating trustworthiness and reliability to customers and partners. Security can become a unique selling point.
- Long-Term Viability: As blockchain technology continues to mature and gain adoption, organizations that prioritize security are more likely to thrive in the long term. Robust security practices can contribute to the sustainability and longevity of blockchain projects.
XI. Additional resource
A. References and Recommended Reading:
- “Mastering Bitcoin: Unlocking Digital Cryptocurrencies” by Andreas M. Antonopoulos – A comprehensive book on Bitcoin and blockchain technology, covering security aspects.
- “Mastering Ethereum: Building Smart Contracts and DApps” by Andreas M. Antonopoulos – Explores Ethereum’s smart contract development and security considerations.
- “Blockchain Basics: A Non-Technical Introduction in 25 Steps” by Daniel Drescher – A beginner-friendly book introducing blockchain technology and security concepts.
- “Blockchain Security: A Concise Introduction” by Sergei Guriev and Julian S. Wright – Offers a concise overview of blockchain security.
B. Links to Relevant Organizations and Communities:
- Blockchain Security Alliance (BSA): A community-driven organization dedicated to promoting best practices in blockchain security. Website: https://blockchainsecurityalliance.org/
- Open Web Application Security Project (OWASP): Although not blockchain-specific, OWASP provides valuable resources on web application security, which is relevant to blockchain development. Website: https://owasp.org/
- Consensus Networks: Offers blockchain security solutions, resources, and a blog focused on blockchain security topics. Website: https://www.consensusnetworks.com/
- Blockchain at Berkeley: A university-affiliated organization that provides educational resources and research on blockchain technology, including security aspects. Website: https://blockchain.berkeley.edu/